Today, the Internet has become almost a daily part of our lives. Many of us are almost dependent on the Internet. It is a great platform for learning new things, social interaction, entertainment, online classes, remote work, or speaking about a cause. It has made our lives easier. Much like the “network of networks” brings in new opportunities with it, there are certain disadvantages. Cybercriminals have become quite savvy in their attempts to gain access to people’s crucial data and devices through malicious ways. The good news is that there are plenty of ways to keep yourself safe on the Internet. It must be remembered that all of these strategies should not be used in isolation, rather they should be used together for the highest Internet security. Let’s deep dive into those strategies.
1. Activate 2-Factor Authentication
The primary purpose of using 2-Factor Authentication (or just, 2-FA) is to protect your online accounts. It is the single most important step that you can take to prevent hacking of your online accounts such as Internet banking, PayPal and other money transfer services, cloud storage accounts, etc. Even if hackers have gotten hold of your user name and passwords, they may not be able to access your online accounts and any important data stored in these accounts. 2-FA adds an additional layer of security to your account by requiring users to prove their identity which acts as a barrier for unauthorized individuals from logging in to your account with stolen login credentials.
Adding 2-FA is usually a simple, straightforward and painless process. The actual steps to set up the 2-Factor Authentication may differ from a website to website. For most services, you can find the option into the security settings or profile options.
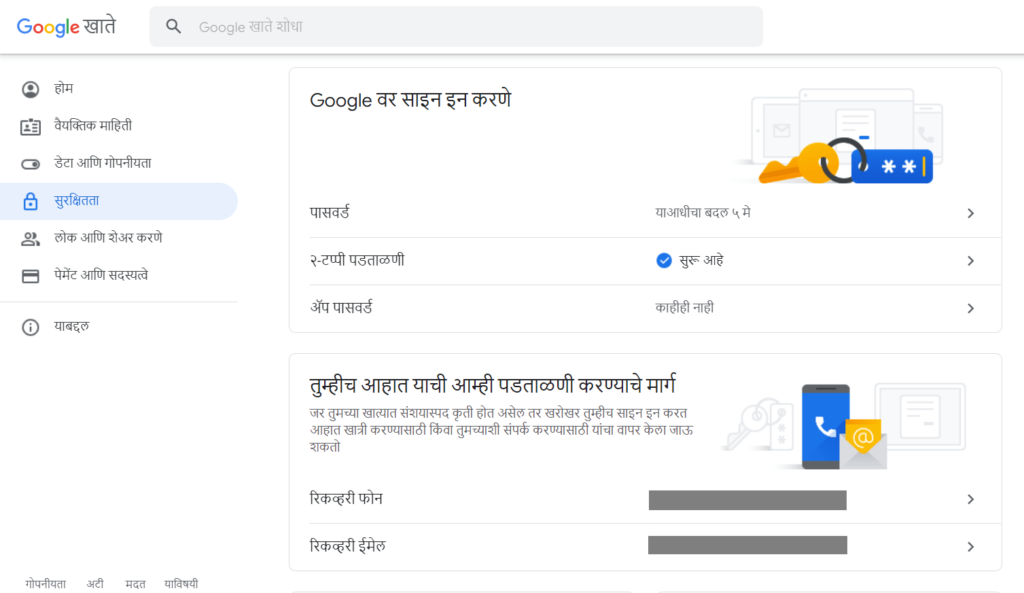
2-FA jumps into action when you try to sign in to your account using a new device or browser that was not used before. With an increasing number of websites supporting (and encouraging to activate) 2-FA, there’s really no excuse not to use this advanced security feature.
You can choose to receive your 2-FA codes either through an SMS, Google Authenticator app or other third-party apps. Each one of them has its own advantages or disadvantages. For example: Google Authenticator is your best bet if you’re constantly facing mobile signal strength issues or traveling from one country to another. On the contrary, codes through SMS can be helpful if your device suddenly stops working and there is no way to access Google Authenticator. In such cases, you can type one of the Backup Codes to login to your account and change the 2-FA method.
2. Use a VPN
While Public Wifis or Free Wifis at airports, railway stations, offices and cafe shops, can be extremely convenient for many, they are not safe. Hackers can position themselves between you and the connection point to access every piece of information you’re sending out, including your important emails, login credentials, credit card details, and other sensitive information.
A Virtual Private Network (VPN) converts your Internet traffic from human-readable plain text into encrypted text so that even if someone were to intercept an unsecured connection, they would not be able to read your data. Encryption transforms human-readable plain text into a ciphertext with a series of randomized alpha-numerical characters.
Proton VPN is one of the best free VPNs. Based in Switzerland, a country known for its strongest privacy laws, Proton VPN places an enormous emphasis on user’s privacy and Internet security. It also has its servers in privacy-focused countries like Sweden and Iceland. Proton VPN claims they have a strict No-Log policy and they don’t monitor user’s Internet Protocol Address (IP Address), session length and other information. And if you haven’t guessed already, Proton VPN is built by the same team of scientists who founded the world’s most popular encrypted & privacy-friendly email service, ProtonMail. Proton VPN offers a free plan too with unlimited bandwidth although there are other restrictions like speed throttling, limited number of servers & countries,. Now, here’s a catch: Proton VPN free plan may not be a good option if you’re mainly using the Internet to watch TV, stream movies, etc.
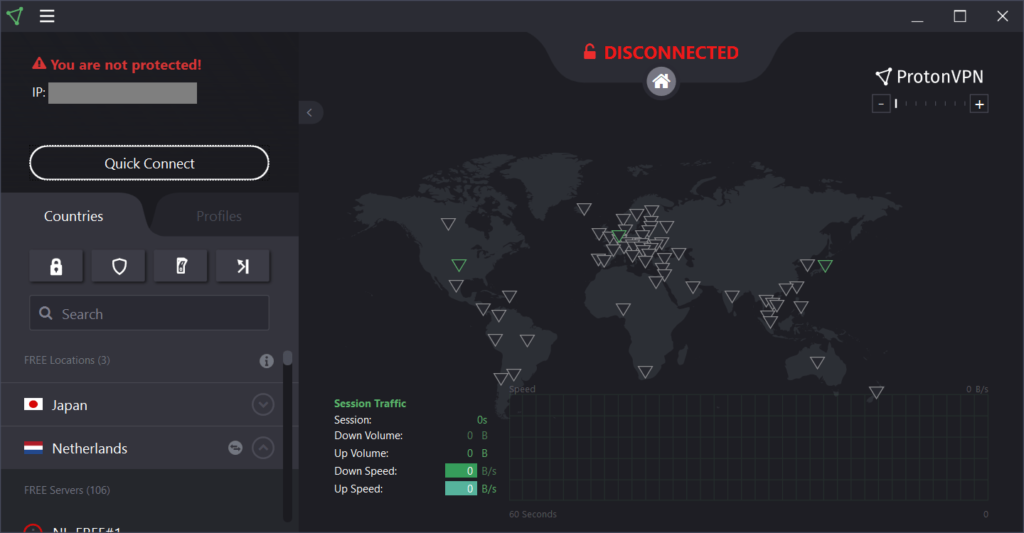
3. Backup your Data
Data losses can occur due to many reasons, such as hardware failure, laptop theft, ransomware attacks and accidental deletion (human errors).
Backing up means to create an identical copy or an archive of your original data. Backups can be extremely handy if your original data or files are lost or become inaccessible. Whether it’s your homework, work files, family photos, you should have some data on your hard disk that’s too precious to lose. Backups are too crucial which is why an entire World Backup Day is dedicated to backups.
A good backup strategy can help you combat data disasters. Here are some best practices while taking backups:
- Always store your backups on another device, separate from the original device. If the backups are stored on the same device as the original data, your backups may not be available or accessible when you need them.
- It’s important to create multiple backup copies rather than a single backup copy which may become corrupt, inaccessible or lost.
- Store your backups on multiple devices rather than storing them all on a single device/ machine. You can sign-up on multiple cloud storage platforms such as Google Drive, Microsoft OneDrive, Dropbox, to store multiple instances of your backups. You can also store multiple backup copies on your SSD, External Hard Disk, DVD-ROM, etc.
- Always encrypt and password-protect your backups to prevent unauthorized modifications or alterations. Popular backup software provides those options. Be sure to memorize and keep the password and/ or Decryption Key file safe at a secure place.
- There are different types of backups. Be sure to choose the one that serves your needs.
4. Use a Password Vault
In order to keep your online accounts secure, security experts across the world often recommend that you-
- Regularly change your passwords
- Have long passwords (for example, 14-24 characters)
- Use complex passwords with a combination of upper/ lower case letters, numbers and symbols. You don’t want others to be able to guess your passwords and access your accounts, do you?
- Don’t use a single password on multiple websites. If one account gets hacked, you risk losing other accounts as well.
Without a Password Vault, it’s not possible to follow all of the above best security practices. It’s simply impractical to remember all different complex passwords. This is where a Password Vault comes into the picture.
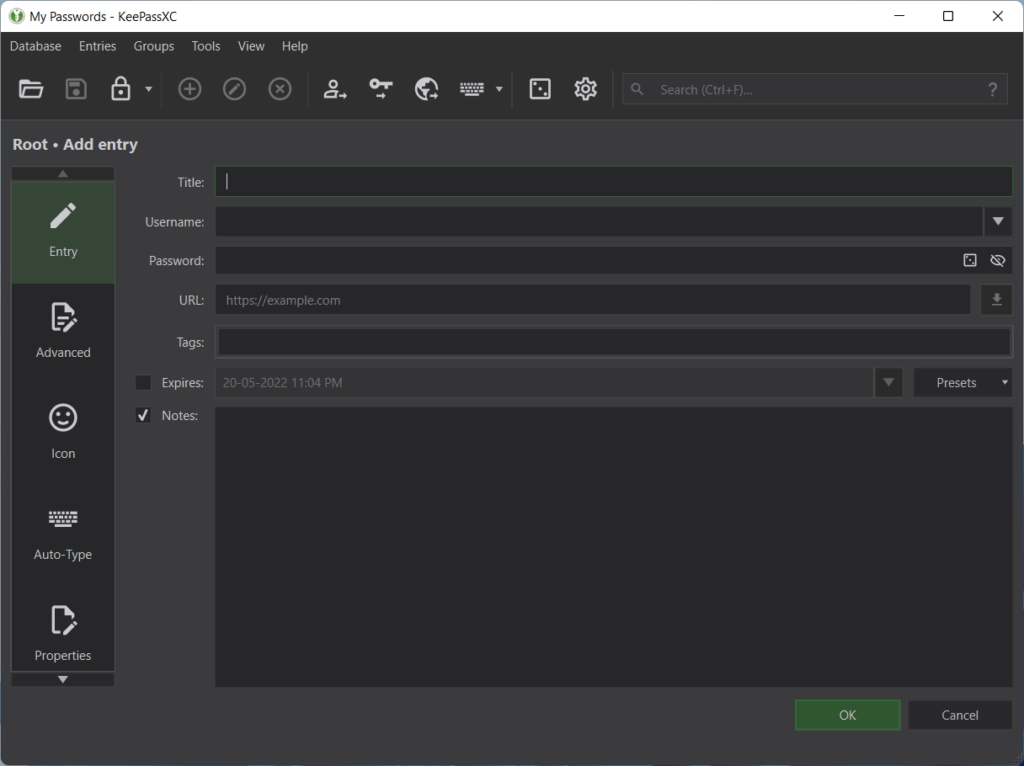
A Password Vault or simply a Password Manager lets you securely store all of your passwords at a single place. Using a Password Vault, you can generate strong, complex passwords and securely store them in a file using the industry-standard file encryption technology. This means that, even if someone has gotten access to your device and your file, they may still be unable to view, copy or export your passwords without knowing the Master Password or without locating the Decryption Key for that file.
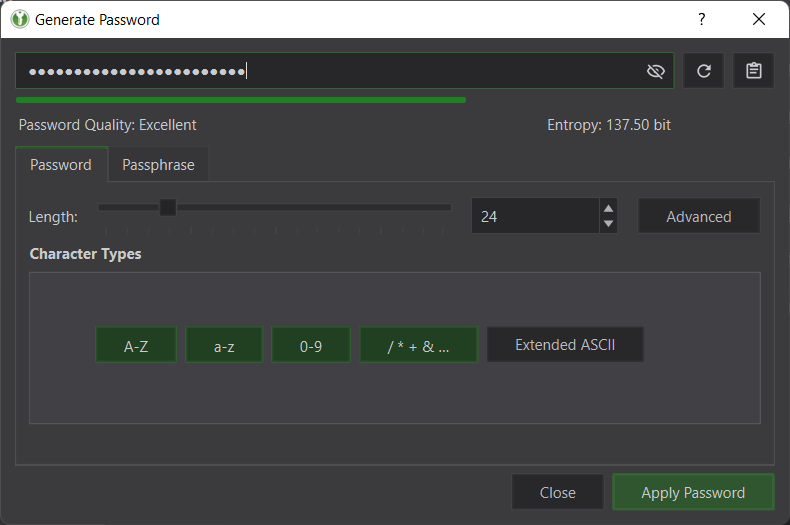
Compatibility: Windows, Linux and Mac
5. Use an Ad-Blocker and Enable Tracking Prevention
Ad-Blocker
Even though the primary purpose of Ad-Blockers is to block distracting ads, they can be incredibly helpful to fight malicious ads as well.
Some ads can be a source of malware. You can actually save your device from being infected with malicious ads that may try to gather your data or infect your device. Ransomware malvertising and CPU-draining crypto mining ads are some of the recent examples.
Enable Tracking Prevention
In addition to the online ads, you might also want to get rid of the trackers. Trackers are commonly used to anonymously track your activities on the Internet. The primary purpose of these trackers is to understand the visitor’s behavior and how they interact with a website. Trackers and ads are sometimes interlinked with each other. For example, some trackers might track you from across multiple websites rather than a single website. This is why, ads keep following you around the web.
Microsoft Edge and Mozilla Firefox automatically enable the Tracking Prevention feature. However, it’s best to confirm whether your Tracking Prevention is already activated or not.
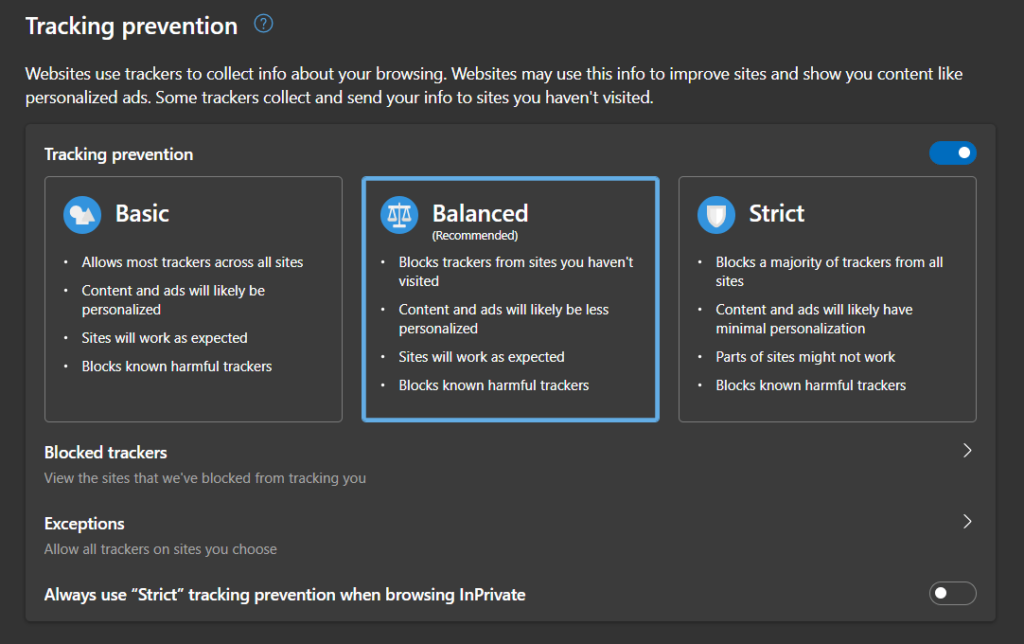
Microsoft Edge:
- Type “edge://settings/privacy” in the Address Bar and press Enter.
- Move the “Tracking Prevention” slider to the right.
- Select the “Balanced” plan.
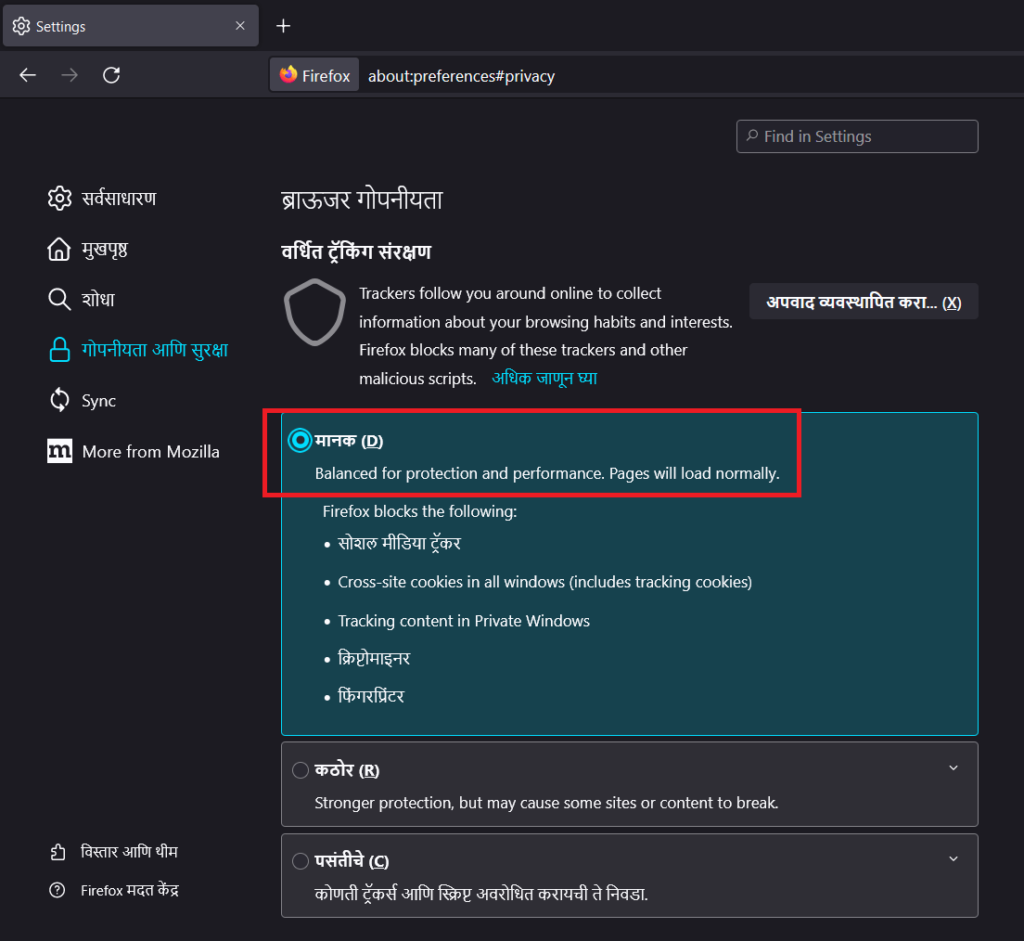
Mozilla Firefox:
- Type “about:preferences” in the Address Bar and press Enter.
- Click on the “Privacy & Security” tab.
- Select the “Standard” plan.
Important: Your browser’s tracking prevention feature might offer multiple layers of protection such as Basic, Balanced and Strict. Strict mode can sometimes break a website. The website may not load correctly, or you may not be able to perform specific actions. For smoother experience, the Balanced plan is recommended. While using the Strict plan, if you suspect that a website is broken due to the tracking prevention feature, refer to the Microsoft Edge and Mozilla Firefox documentations to learn how to exclude that particular website.
6. Use a Sandbox Software
A Sandbox software creates an isolated testing environment to test computer applications or files downloaded from untrusted sources. It offers an additional layer of security to protect your host system from applications or files that come from unknown/ untrusted vendors.
It’s highly recommended to open your web browser into a Sandbox software while visiting untrusted/ suspicious websites or while downloading suspicious files in order to prevent harm to the host system and other installed applications.
Download Sandboxie Plus (Free)
7. Use a Firewall Protection
A Firewall keeps your computer safe on the Internet, particularly network-based threats. It permits only certain types of data to cross and filters out any unsolicited network traffic from uninvited guests trying to come in. Similarly, it also alerts about suspicious outbound connection attempts by software applications installed on your machine. Windows Firewalls is pre-enabled by default. However, it’s a good idea to re-confirm the same from your computer settings.
8. Keep Windows Defender Up-to-Date
Modern versions of Windows come with a comprehensive Windows Defender security software pre-installed with real-time scan, app & browser control, parental controls and many other in-built features. Make sure your Windows Defender is enabled and up-to-date with the latest virus definitions.
9. Update your Browser & System
It’s important to update your web browser and operating system on a regular basis to keep your computer protected from phishing attacks, viruses, spyware, adware, trojans and identity thefts.
Browser and operating system updates include not just performance, UI and functional updates, but also important security updates that fix crucial vulnerabilities and bugs that hackers can exploit to steal your sensitive data or gain access to your system.
10. Identify Malicious Emails
Email is an important tool for communication. Every day, millions of emails are sent — most of which are legitimate and harmless. However, cybercriminals are constantly exploiting human nature using various social engineering strategies to trick people into clicking malicious links or malicious attachments to steal personal or business data, login credentials or infect devices.
Here are some hints that may help you identify a malicious email:
- Urgency: A cybercriminal doesn’t want you to think. This is why a malicious email urges people to take an urgent action. Links to such call-to-action buttons can be dangerous. Here are some sample subject lines: “Urgent action required”, “Your account will be deactivated within 24 hours. Act fast.”
- Domain Spoofing: Cybercriminals often deceive people by creating domains that appear like legitimate businesses. However, a closer look will help you find that the sender’s address is illegitimate with slightly altered characters impersonating a genuine business or individual. For example: A cybercriminal may impersonate Microsoft by sending an email from [email protected] (notice the double “I”).
- Malicious Attachments: A cybercriminal may urge you to download and open the email attachments which may contain malicious scripts, ransomware, trojans, viruses, or other dangerous threats. Never open email attachments from unknown people. Even if it’s from someone you know, it’s best to scan it for viruses. If you’re unsure about the legitimacy of an email, you may contact the sender via phone to confirm.
- Macros: Cybercriminals love to hide their malware into popular file formats that no one would suspect. For example: A Word Document, a PDF or a Zip file. A Word Document or PDF may contain dangerous macros that can perform a set of actions including mouse clicks and keystrokes. The good news: Microsoft Office disables the macros by default.

Leave a Reply
You must be logged in to post a comment.